Gordon Myers
Articles on Life, Truth, Love, Computers, and Music
How to Sign a Java Applet
I am not a Java developer. I'm a PHP developer who happens to have written a Java applet in NetBeans. (Apparently it's not technically an applet, but a "Web Start application;" I don't know what the difference is and I don't care.) For a long time my applet was "self-signed," until Java changed their policy last year, no longer allowing self-signed applications after a certain cutoff date. That meant I started seeing nasty warnings like this:
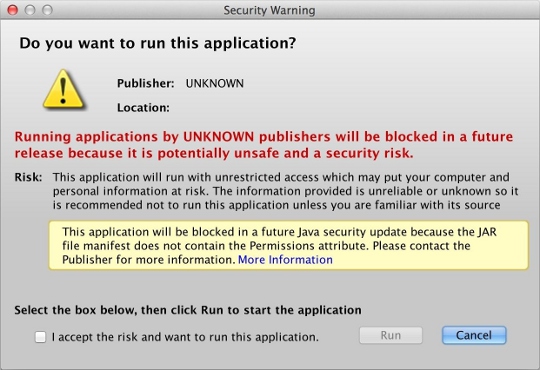
...which eventually changed into this:
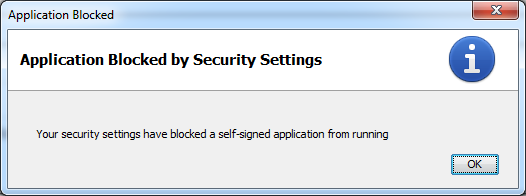
So I had to purchase a Code Signing certificate from some signing authority like GoDaddy or Thawte or Comodo. I went with GoDaddy. What I learned along the way is that Java developers are the worst kind of developers when it comes to documentation. They do have a lot of documentation, but it's totally useless. They have 10,000 word articles that effectively say nothing at all. Unless you already understand everything and don't need to be reading documentation in the first place, it's virtually impossible to figure out how anything works. So this blog post is an effort to offer up what I learned along the way while trying to sign my Java applet, from and for the developer who knows nothing about Java boilerplate.
After purchasing the certificate from GoDaddy and trying, for hours, to make two cents of their installation instructions, here's what I learned: you have to use Firefox to install your certificate. I don't know why; I don't care why; you have to do it. Their tech support technician had me navigate to certs.godaddy.com, where I had to install the Code Signing Certificate into Firefox. Originally I had tried to download a "backup copy" of the certificate directly. It gave me a choice of a DER file (actually an SPC file) or a PEM file. But these files will not work. Apparently these files save the certificate in PKCS#7 format, which isn't good enough for some reason. You need a file in PKCS#12 format, which requires you install it into Firefox and then use Firefox to export the file. (Why you can't just download that file directly, I do not know.) So I had to re-key my certificate, install it into Firefox, and then go to Tools > Options > Advanced > View Certificates.
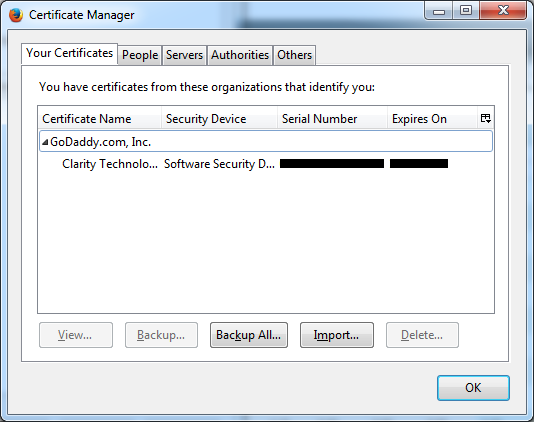
From there I located the certificate (pictured above), clicked "Backup..." which let me save it in PKCS#12 format, as a P12 file. Apparently this is also called the PFX format.
In the GoDaddy installation instructions, I had been trying to use their "Approach #1" to install the certificate, when I originally downloaded the PEM file. As far as I can tell, this approach is a wild-goose chase. I would move the PEM file into my Java directory, open up a command prompt in the same folder, and then try this command:
| Informational Only - Ignore This Part |
|---|
| > keytool -import -trustcacerts -keystore NewKeystoreFile.jks -storepass myPassWord -alias MyAlias -file cert.pem |
That would generate a file called NewKeystoreFile.jks in that same directory. Then I would go into NetBeans (which I used to build my applet), select Project Properties, go to Application > Web Start > Signing > Customize, and plug in that file:
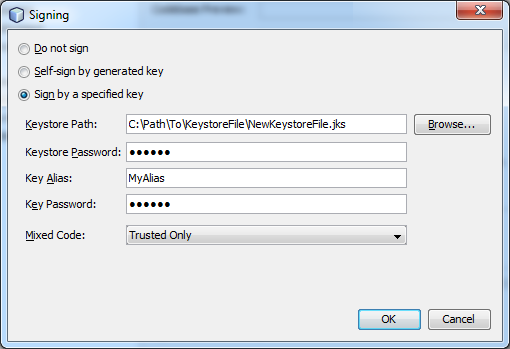
But when I did a Clean & Build, my applet would not compile, and I would receive the following error:
jarsigner: Certificate chain not found for MyAlias. MyAlias must reference a valid KeyStore key entry containing a private key and corresponding public key certificate chain.
Apparently the PEM file (PKCS#7 format) doesn't cut it. It installs the certificate, but not the private key, into the keystore. I don't know what that means, but what it means is that it's broken and my applet won't work. So instead, I had to use the aforementioned P12 file I got from Firefox. There are no instructions on how to do this in GoDaddy's documentation. I was fortunate enough to discover a set of instructions provided in a blog post by someone from a company called JAMF Software. I don't know who they are but that blog post was a godsend.
So I copied my cert.p12 file into my Java directory, opened up a command prompt in the same folder, and used this command:
> keytool -v -list -storetype pkcs12 -keystore cert.p12
That command doesn't actually do anything, other than print out lots of information about the cert.p12 file on the screen. The only purpose of running that command is to find out what alias name GoDaddy decided to use in their certificate. In my case, because I work for Clarity Technology Group, GoDaddy used the following obnoxiously long alias name:
clarity technology group, inc.'s godaddy.com, inc. id
Whatever your alias happens to be, you need it for the very next step, which is why you run that first command to determine what it is. And if it's got spaces and apostrophes, etc. like mine did, you'll need to encapsulate it in double quotes. The next command, which is the crux of this whole process, is this:
> keytool -importkeystore -srckeystore cert.p12 -srcstoretype pkcs12 -srcalias "clarity technology group, inc.'s godaddy.com inc. id" -destkeystore NewKeystoreFile.jks -deststoretype jks -deststorepass myPassWord -destalias MyAlias
That generates a file in that same directory called NewKeystoreFile.jks, which you can then move out to some other directory and plug into NetBeans as shown above. And then it should actually work! I was able to do a Clean & Build without any error messages. And now, when I load up my applet, the popup message looks like this:
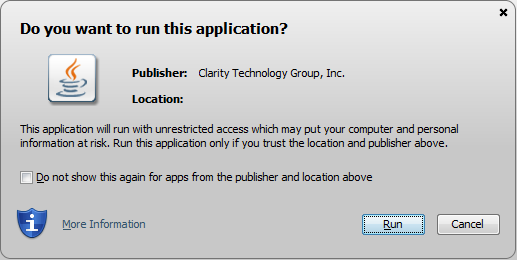
I'm going to write a later blog post about how annoying Java is. I am annoyed. Stay tuned.
3 Comments from the Community:
Congratulations! - that was a convoluted process, wasn't it? The only thing worse than no documentation is inaccurate documentation...
Thankfully I don't have to develop in Java. Unfortunately I have to support Java-based broadcast systems. They greatly underperform given the high-powered hardware in use. And tend to throw weird error messages. (or simply silently stop working :( )
"I'm going to write a later blog post about how annoying Java is. I am annoyed. Stay tuned."
I will.
Great Article. Are there free certificates for signing Java applets?
No, unfortunately there is no such thing as a free signing certificate. That would actually defeat the purpose of them in a sense. As I mentioned at the beginning of the article, there is a concept of "self-signing" your own code, which is free, but Java has locked that down as insecure -- hence the purpose of this article. The idea behind signing is that you have a verified company that everyone trusts signing the code. You, as a developer, don't actually provide that company with the code, but you do provide them with your contact information -- a valid address and phone number, which they verify, and then they give you a certificate at a cost to sign your code with. That doesn't strictly ensure that your code won't be malicious, but it does ensure that if you code is malicious, people will report it to the signing authority, and you can be held accountable since your contact information is on file and has already been vetted as being valid.